Cross-Site Scripting (XSS) Vulnerability
Cross-Site Scripting (XSS) Vulnerability
Cross-Site Scripting (XSS) is a type of security vulnerability commonly found in web applications. Beside SQL injection its probably the most common one in the world of cyber security. It allows attackers to inject malicious scripts into web pages viewed by other users. XSS is one of the most common vulnerabilities, and it can lead to severe consequences, including data theft, account compromise, and system manipulation.
Types of XSS
There are three main types of XSS attacks:
Stored XSS (Persistent XSS)
-
How it works: The malicious script is stored on the server (e.g., in a database) and served to users every time they access the compromised page.
- Example: An attacker injects a malicious script into a comment section of a website. When other users view the comments, the script executes in their browsers.
- Impact: More dangerous due to its persistence and ability to affect multiple users.
Reflected XSS
How it works:The malicious script is embedded in a URL and reflected off the server. The attack is typically delivered via phishing emails or links.
Example: A URL like http://example.com/search?q=
alert("XSS");
causes the browser to execute the malicious script.
Impact: Can target specific users but is less persistent compared to stored XSS.
DOM-Based XSS:
How it works: The vulnerability exists in the client-side JavaScript, where the script dynamically modifies the Document Object Model (DOM) without proper sanitization.
Example: A web app takes input from the user, like a search query, and dynamically updates the page without sanitizing the input.
Impact: Harder to detect since it doesn't involve the server, but still dangerous.
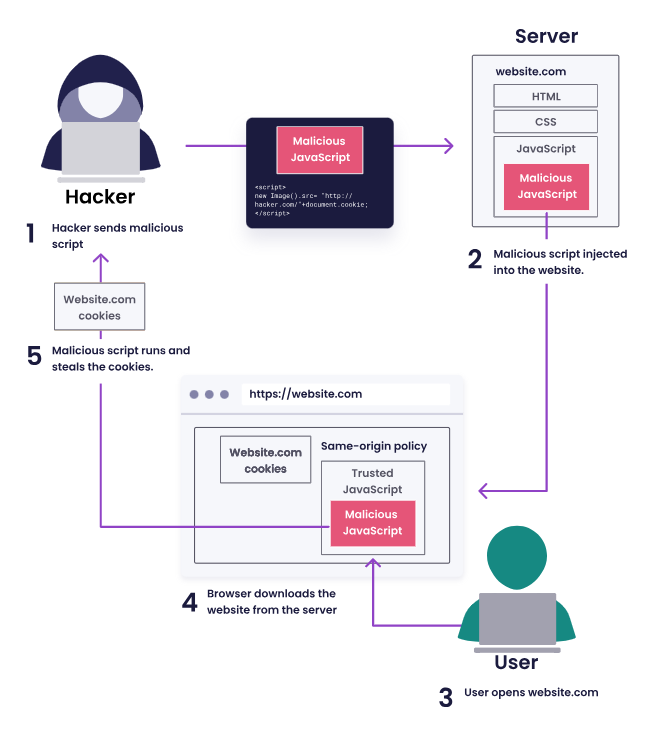
How XSS Works
Injection of Malicious Code: An attacker identifies an input field or URL parameter where they can inject a script.
Execution in the Victim's Browser: When a user interacts with the compromised web page, their browser executes the malicious script.
Outcome:
Stealing cookies, session tokens, or sensitive data.
Defacing websites or displaying fake information.
Redirecting users to malicious websites.
Exploiting other vulnerabilities in the user's environment.
How to Prevent XSS
Input Validation and Sanitization
Validate all user inputs on the server and client.
Reject inputs containing unexpected characters (e.g., <, >, script).
Output Encoding
Encode user input before displaying it in the browser to prevent script execution.
Use libraries like OWASP's Java Encoder for Java-based applications.
Use HTTP-Only Cookies
Prevent JavaScript from accessing cookies by marking them as HttpOnly.
Content Security Policy (CSP)
Implement a CSP to restrict the sources from which scripts can be executed.
That's it, stay safe!
Luka Vukovic